The race is on to perfect quantum computing. It will make your bank passwords and all existing security methods useless.
The Hutch Report has a fascinating 44-page PDF on Quantum Computing.
Read What Happens When Quantum Computing and AI Merge?
If perfected, existing methods of encryption will cease to work. Your bank account password and passwords to cryptocurrencies will easily be hackable.
The ability to break the RSA coding system will render almost all current channels of communication insecure.
This is a national security threat.
The benefits are also huge: Quantum computers will be superior at hurricane detection, airplane design, and in searching DNA for markers to help find cures for diseases such as Autism, Alzheimer’s, Huntington’s, and Parkinson’s.
Classical Computers
Classical computers use strings of 0’s and 1’s with a single digit a "bit" and strings of bits a "byte". A bit is either a one or a zero.
Excerpts from the Hutch report now follow. I condensed 44 pages to a hopefully understandable synopsis of the promise and problems of quantum computing.
Quantum Background
Quantum computing does not use bits but uses qubits which can be one, zero, or both zero and one at the same time. This state or capability of being both is called superposition. Where it gets even more complex is that qubits also exhibit a property called entanglement. Entanglement is an extraordinary behavior in quantum physics in which particles, like qubits, share the same state simultaneously even when separated by large distance.
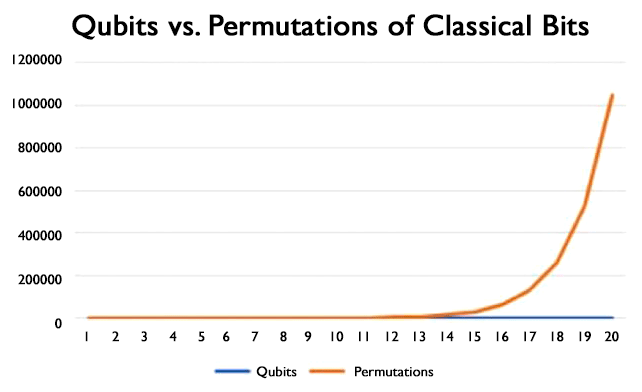
As a comparison, a classic computer using bits of zero and one can only store one state at a time and can represent 2n states where n is the number of bits. In the case of two bits, this would be 2*2 which is four states: 00, 01, 10, 11.
A normal computer would require four operations to examine each state. Two qubits could store the four states at one time. When the number of states is low there is not a major processing difference. As the number of possible state combinations increases, the difference in processing time between quantum computers using qubits and a classic computer using classic bits increases exponentially. The following chart depicts this well showing that 20 qubits can represent simultaneously over 1 million permutations of classical bits.
Quantum computing is in its infancy and is probably comparable to where classic computer technology was in the 1960s and 1970s where it took an entire room to house a computer.
The qubits are extremely sensitive to interference and one of the main challenges in constructing quantum computers is creating an environment with no interference and enabling stable qubit states. To achieve stable environments, the majority of quantum computer platforms require vacuum states as well as superconductivity. When superconductivity is deployed this, in turn, requires cryogenic cooling (e.g. refrigeration to extremely low temperatures).
In addition, each quantum computer must be specifically built to run a specific algorithm. To change or run a different algorithm requires rebuilding the computer. Two of the better-known algorithms built to date are Grover's Algorithm, which uses quantum computing to conduct searches on unstructured databases much more quickly and efficiently than a classic computer; and Shor's Algorithm which is an algorithm for finding prime factors.
Read also Podcast: Quantum Computing Takes Flight
Although the U.S. currently remains at the forefront of quantum information science, their lead is slipping quickly as other nations step up efforts to get there first. China holds the top two positions in the Top 500 list of the world's fastest computers and the Chinese understand very well the potential power that quantum computing promises. For this reason, they have allocated extensive funding towards the goal of producing a functional quantum computer before anyone else. On 37 hectares (nearly 4 million square feet) in Hefei, Anhui Province, China is building a $10 billion research center for quantum applications. This news comes on the heels of the world’s first video call made via quantum-encrypted communications and the completion of a quantum-encrypted fiber optic trunk cable.
Factoring Large Numbers Very Rapidly (Shor's Algorithm)
[Mish Note: current encryption methods involve multiplication of extremely large prime numbers. Bitcoin "mining" rewards the computer that solves such mathematical puzzles first.]
Utilizing a specialized algorithm such as mathematician Peter Shor’s, a quantum computer can compute large integer factoring in polynomial time versus classical computing’s sub-exponential time. Therefore, quantum computers have the ability to solve, in a quick time frame, problems that were previously too difficult to solve in any reasonable time. Typically, these are problems involving extraordinarily large amounts of data or large amounts of possible combinations.
Aviation
Large aircraft companies are working to develop quantum algorithms that will greatly reduce research time in achieving aeronautical efficiencies. For example, the potential to predict the flow of air over a wing, something that would take classical computers more than 7 years of computing time. This would enable the development of new robust efficient aircraft with low noise and CO2 emission to be achieved in a much shorter time period. It currently takes several years for engineers to test the design of an airplane wing, and model airflow at different angles and speeds. A good design will reduce operating costs, save fuel, which in turn means less carbon emissions.
Secure Communication Technology
Once quantum computers become readily available today’s security encryption protocols will be easily broken. Quantum-resistant and improved cybersecurity techniques are being developed. Therefore, the impact of cyber-attacks on artificial intelligence and major databases and other sensitive systems may be significantly reduced.
Weather Forecasting
The flow of air, water or other liquids are the foundation of many practical applications. The current underlying models are based on Navier-Stokes equations which describe the motion of viscous fluid substances and are extremely challenging problems in computational physics. Quantum computer simulators could potentially provide models for a large number of areas such as turbulence, flow in industrial furnaces to the protection of low-lying countries for sea-water flooding.
Medicine and Healthcare
Quantum computing ability to model molecular interactions at an atomic level will allow us to gain insight towards developing new medicines and a greater understanding of diseases such as cancer, Alzheimer’s, Huntington’s, and Parkinson’s. In order to find breakthroughs for treatments, it is crucial to understand the structure of proteins and how they fold. Simulating protein folding is extremely expensive in terms of time and cost, which include access to supercomputing facilities. A quantum computer should be able to work out the best possible treatment for a given patent, achieving not only a more precise result but, in theory, much faster as well.
Mish Comments
Quantum computers offer many promises. They also pose security threats.
The first country that succeeds could hack into bank accounts or the Pentagon.
How close are we? I have no idea. Nor do I know if they will ever work, but I strongly believe they will.
This I do know: It is a national security threat if China perfects quantum computing first.
I initially wrote "A quantum computer could also mine nearly every bitcoin," but a reader disputes that. See the addendum below.
Addendum
Reader ThroughNothing adds these thoughts.
Hey Mish, thanks for your posts, I’ve been a longtime reader and have gained a lot of value and education from your posts. I do want to point out that there is currently no known quantum algorithm that can “break” sha256, which is the algorithm that bitcoin uses for mining. Additionally, if you don’t use a bitcoin address more than once, the private key to your coins remains “quantum resistant”, because your public key (which can be used by a quantum computer to “factor” your large number) is not revealed to the network until you spend coins from an address. Until that point, only a hash of your public key is provided, which, similarly to sha256 hashes mentioned above, cannot be “broken” by known quantum algorithms. I know this may be technical for your audience, but I think those are important details. For my background, I’ve been in computer software and security/cryptography for over 12 years now. Thanks again!